Where are we at in the process of knowing what we didn’t know and guessing if what we do know is now on the list of what we don’t know, and how much of what we put on that list is really what we should know?
Can we toss out stuff and take it back later if we see it’s true? Yes. Can we collect stuff now and think it’s true and toss it out later if we see it’s not true? Yes. What does that make us? HUMAN!!! SMILE… HERE WE GO AGAIN….

Aside from being insane, this is highly unconstitutional! Fines for stopping thieves in your store? Good grief!
Which bring us to… our civil rights!
What’s up with this?
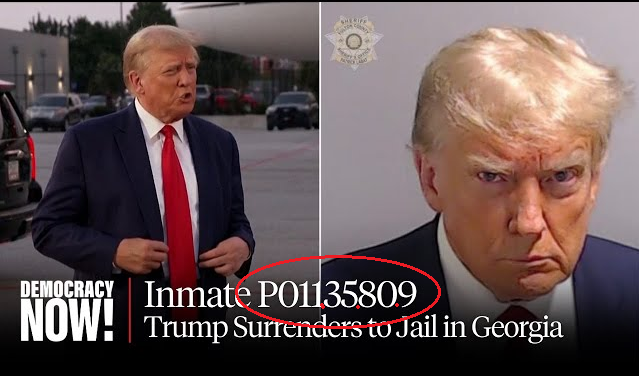
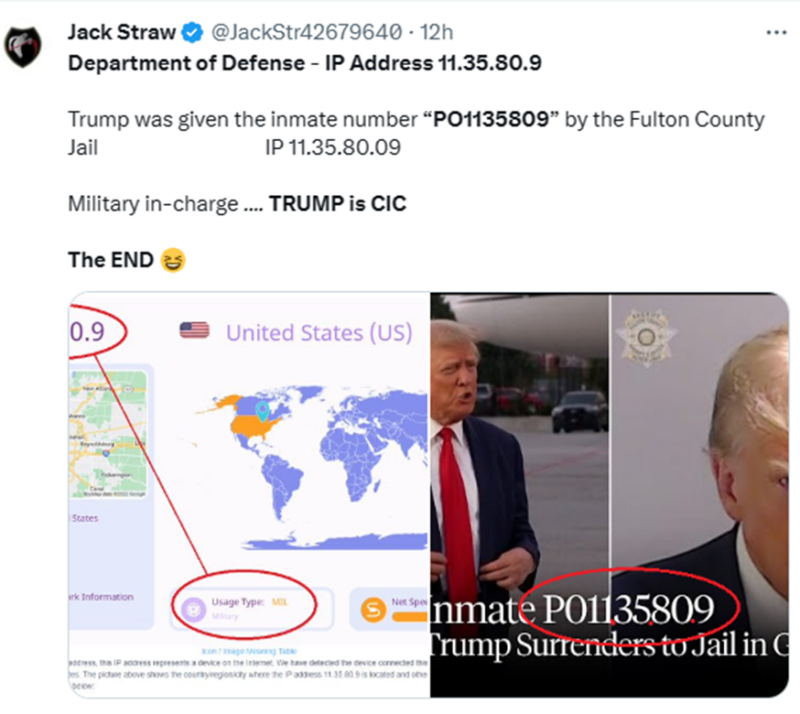
What do you discern?
An IP address is not considered in the same league as fingerprints or social security numbers. Some have likened an IP addresses to zip codes rather than personal identifiers. IP addresses link to computers or devices that can be used by any number of people.
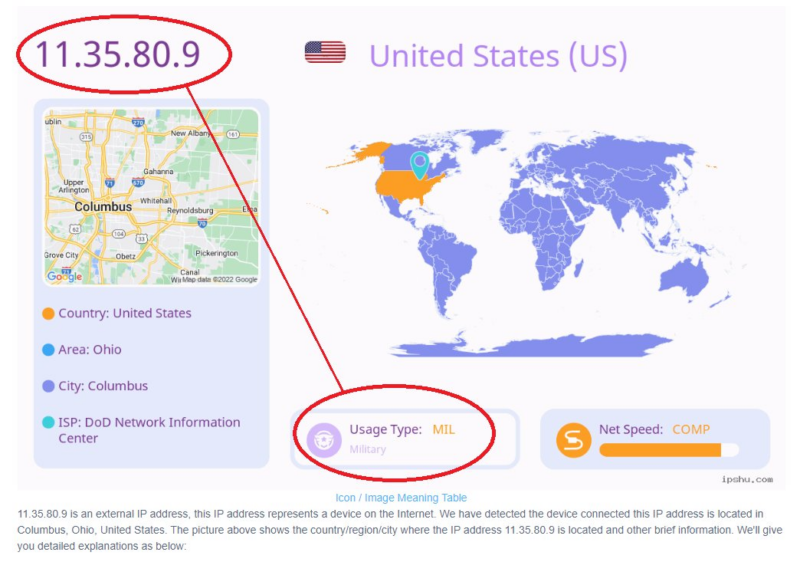
Tracking Criminals with Internet Protocol Addresses: Is Law Enforcement Correctly Identifying Perpetrators?
By Erin Larson, North Carolina Journal of Law and Technology:
An IP address is analogous to a phone number in that both serve as a unique identifier for a particular device.
1 Similar to how a phone number is assigned to a telephone device, an IP address is
assigned to a specific computer.
2 Furthermore, each router that a device uses to connect to the Internet also has an IP address assigned by the Internet Service Provider (“ISP”), comparable to how a phone number is assigned by the phone provider.
3 Just as a person would dial a given number to reach a specific individual, the assigned IP address allows various devices connected to the Internet to “talk” to each other so that data can be shared among them.
4 Each time a user visits a website, the website logs their IP address.
5 With this information, the website can keep a record of who visits the site via tracking the IP addresses that accessed the site, similar to how phone companies keep a log of their users’ calls.
VI. CONCLUSION
IP addresses are useful for locating criminals and provide a stepping-stone for launching subsequent investigations. Nevertheless, judges should persist to request more specific information before granting search warrants. With the advent of
freely available information regarding users’ online conduct, it is not unduly burdensome for officials to obtain additional information to support pending searches. With an IP address, for example, officials can first subpoena the ISP for customer information which can then be used to corroborate a suspect’s online identity. From there, signal monitoring devices can be used to observe where the suspected online conduct originates. These additional steps are necessary to ensure proper judicial prudence when conducting new investigations.
As techniques become more intrusive, both officials and users must be wary about privacy concerns. Users must take extra steps to ensure their networks are secured and should actively check to see if any unauthorized users are accessing their network. Additionally, law enforcement officials carry a heavy burden themselves and must tread carefully so as not to cross into unconstitutional search territory. IP addresses do not always provide concrete details about a suspect’s identity, so caution should be used when invasive techniques are used to obtain a suspect’s IP address. As seen in cases where criminals use dark web browsers, IP addresses can easily be relayed among various different computers across the country or can be re-routed to another device. Officials should be hesitant to use invasive techniques to obtain this information, as it could prove fruitless to their search, particularly given some courts’ decisions to suppress evidence because legal procedures were not followed.
207 Similarly, if officials successfully bring charges against a suspect but are
compelled to reveal specific details about their search techniques, they may choose to dismiss the criminal charges against the suspect, rather than have to reveal their method. 208 These concerns, among others, are shaping a new landscape for investigating criminal activity online. IP addresses alone should not provide sufficient probable cause to obtain a search warrant given their unreliable nature.
So let’s see that one more time…. ponder it.
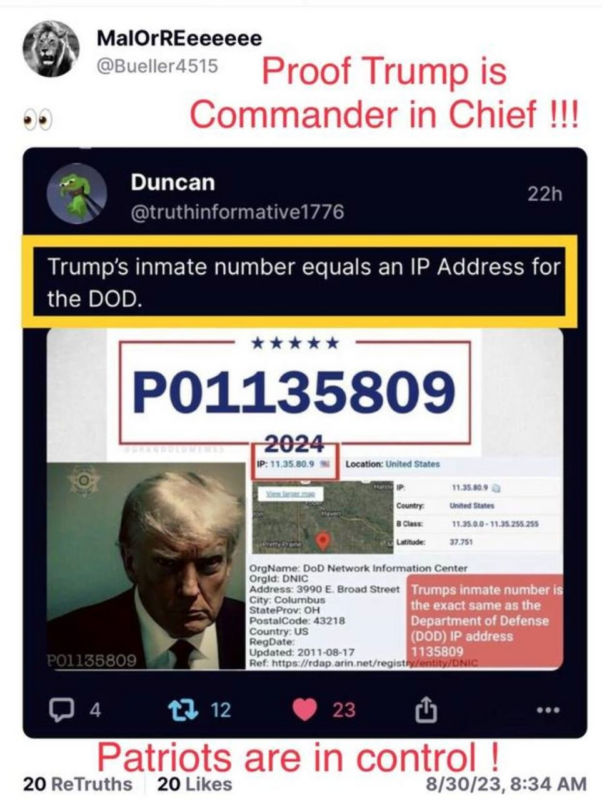
What did President Trump mean by “Partially Corrupt” System of Justice?
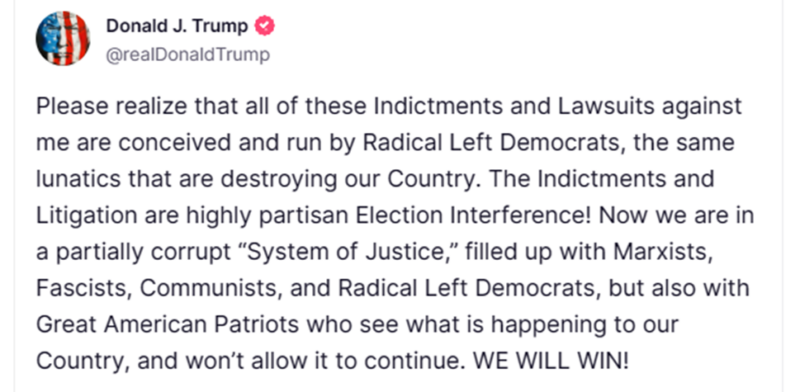
People are starting to connect the dots fast now… and see the patterns. It all changes when it’s in your own back yard!
Adding up the facts… connecting some dots. See a pattern?
This is two weeks old, but it is backed with information that people are still asking about.
And now, the most important message of the day… from Pastor Melissa Scott. Right from the Word. No twists, no hype, just what it says.
How God works according to the Word of God. Fear not. God’s ways are not man made up ways. Amen.
Remember, God does things orderly and is not the least bit confusing. Man and the devil made all that type of mess. Come out from her my people!
Keep on pressing into the Kingdom of God! Press, press, press!
Dianne

